Tunnel Wireless Ad Hoc Network Communication Solution
I. Overview of the Plan
In the complex environment of tunnels, traditional communication networks are difficult to deploy and prone to damage. However, wireless ad hoc networks do not rely on pre-established infrastructure and can quickly and autonomously form a network. Nodes can dynamically establish connections to achieve multi-hop data transmission. They are particularly suitable for scenarios such as tunnel construction and disaster emergency response, providing reliable communication guarantees for personnel and equipment within the tunnels.

II. Network Architecture Design
The network architecture adopts a hierarchical structure, consisting of the bottom node layer, the middle routing layer and the upper application layer. The bottom node layer includes various terminal devices deployed within the tunnel, such as handheld terminals, vehicle communication devices, sensor nodes, etc., which are responsible for data collection and transmission; the middle routing layer is composed of high-performance routing nodes, which undertake the tasks of data forwarding and path optimization to ensure efficient data transmission; the upper application layer is oriented towards users and provides diversified communication services such as voice calls, video monitoring, and data interaction. The layers communicate through standard protocols to ensure the compatibility and scalability of the network.
III. Application of Key Technologies
(1) Multi-hop Routing Technology
The tunnel environment is long and narrow with numerous obstacles, and signals are prone to being blocked. The multi-hop routing technology enables data to be forwarded multiple times between nodes to bypass obstacles and find the optimal transmission path. By adopting the Dynamic Source Routing Protocol (DSR), nodes do not need to maintain the entire network's routing information. Through on-demand path discovery, it reduces routing overhead and improves network efficiency. At the same time, combined with the link quality assessment mechanism, it monitors the link status in real time. When the quality of a certain path declines, it automatically switches to the backup path to ensure the continuity of communication.
(2) Anti-interference Technology
There are various electromagnetic interference sources inside the tunnel, such as construction equipment and power systems. By using frequency-hopping spread spectrum (FHSS) and direct sequence spread spectrum (DSSS) technologies, the signals are transmitted across multiple frequency bands to reduce the impact of interference. At the same time, the intelligent antenna technology is utilized to adjust the radiation direction of the antenna according to the direction of the signal source, enhancing the strength of the useful signal and suppressing the interference signal, thereby improving the reliability of communication.
(3) Power Control Technology
To extend the battery life of nodes and reduce interference between nodes, power control technology is introduced. The transmission power is dynamically adjusted according to the distance between nodes and the quality of the link. When communicating at a short distance, the power is reduced to decrease energy consumption and minimize interference to other nodes; when communicating at a long distance or when the link quality is poor, the power is appropriately increased to ensure the stability of data transmission.
IV. Equipment Selection
(1) Wireless Ad Hoc Network Node Devices
Select node devices with high integration, low power consumption and strong anti-interference capabilities. For example, industrial-grade wireless ad hoc network modules, which support multiple communication frequency bands (such as 2.4GHz, 5.8GHz), have a transmission rate of up to several tens of Mbps, and the operating temperature range is from -40℃ to 85℃, meeting the usage requirements of the harsh environment in tunnels. The node devices should have waterproof, dustproof and shockproof designs, with a protection level of above IP67.
(2) Key routing nodes
The backbone routing nodes must have strong processing capabilities and data forwarding capabilities. High-performance industrial-grade routers should be selected, equipped with multi-core processors, large-capacity memory and storage, and support multiple routing protocols and network interfaces (such as Ethernet, fiber optic interfaces), enabling seamless connection with external networks. At the same time, a backup power supply is provided to ensure that the system can continue to operate for several hours in the event of a sudden power outage.
(3) Terminal devices
Select the appropriate terminal equipment according to different application scenarios. For example, handheld walkie-talkies with wireless ad hoc network function are suitable for real-time voice communication among personnel in the tunnel; portable data collection terminals can be connected to various sensors to achieve real-time collection and transmission of environmental parameters (such as temperature, humidity, harmful gas concentration) and equipment status data; vehicle communication terminals are installed on tunnel construction vehicles or inspection vehicles to enable communication between the vehicles and the control center.
V. Network Deployment and Implementation
(1) Preliminary Planning
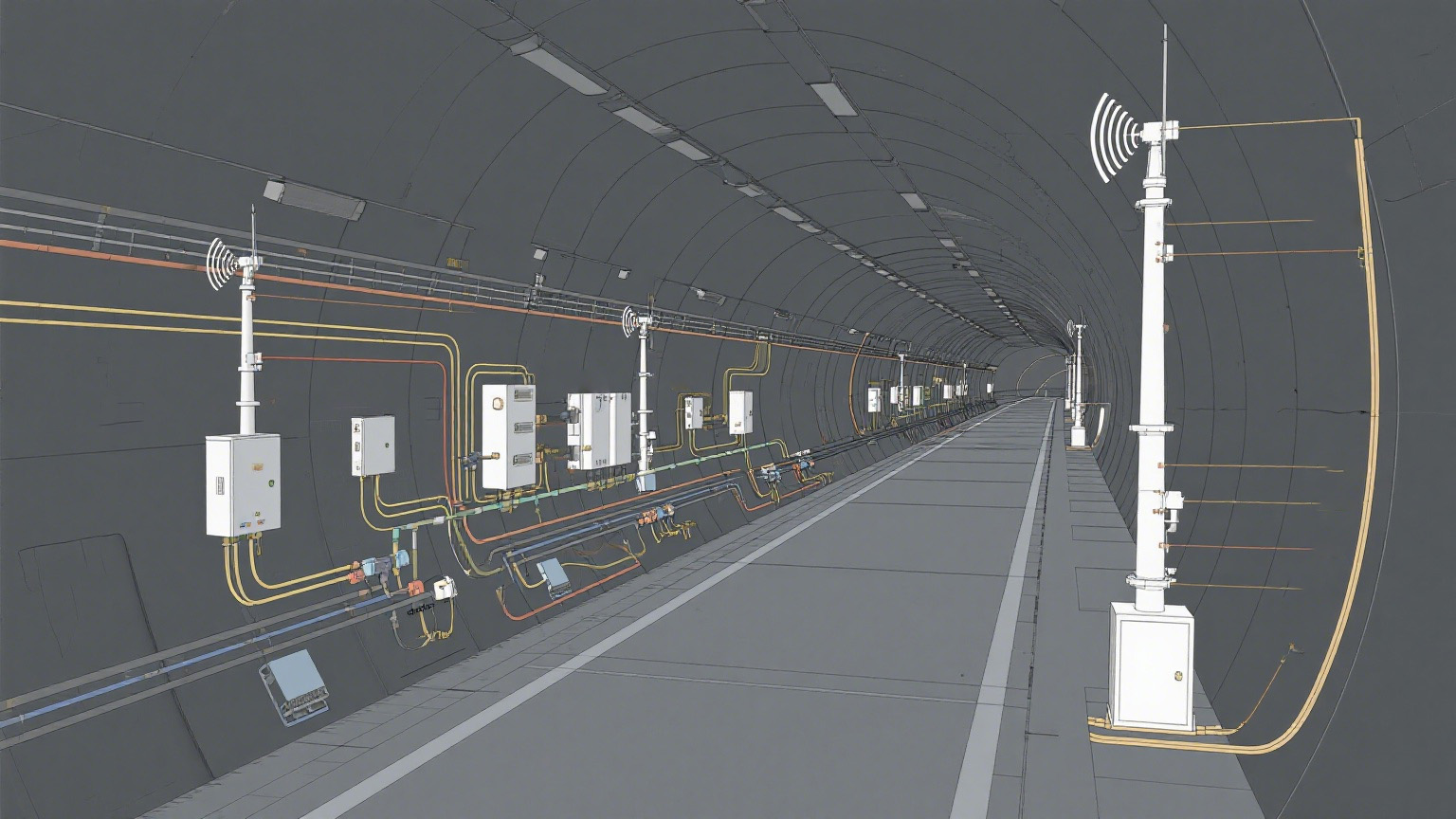
Before the construction or renovation of a tunnel, a field survey of the tunnel is conducted to obtain information such as its length, structure, number of bends, and distribution of construction equipment. Based on communication requirements and environmental characteristics, the deployment locations and quantities of nodes are planned to ensure no signal coverage gaps. For long tunnels, a backbone routing node is deployed at regular intervals (such as 200 - 300 meters) and multiple terminal nodes are deployed in areas with frequent human activities and key construction points.
(2) Equipment Installation and Commissioning
According to the planning scheme, wireless ad hoc network node devices and backbone routing nodes are to be installed on the tunnel walls, tops or equipment. The installation of the devices must be firm and reliable to avoid loosening due to vibrations in the tunnel. After installation, the devices need to be debugged, and network parameters (such as frequency band, channel, node ID, etc.) are configured. The communication connection and data transmission performance between the nodes are tested to ensure the normal operation of the network.
(3) Network Optimization
By using network monitoring tools, the operating status of the network can be monitored in real time, and network performance indicators (such as throughput, latency, packet loss rate, etc.) can be analyzed. Based on the monitoring results, the network can be optimized and adjusted, such as adjusting the transmission power of nodes, optimizing routing paths, increasing or reducing the number of nodes, etc., to improve the overall performance and stability of the network.
VI. Network Management and Maintenance
Establish a network monitoring center and use dedicated network management software to conduct real-time monitoring of the tunnel wireless ad hoc network. The monitoring contents include node status (online/offline, battery level, signal strength), data traffic, routing information, etc. When abnormal situations such as node failure or link interruption occur, the system will automatically alarm and locate the fault location, facilitating maintenance personnel to handle the faults promptly. After the maintenance personnel receive the fault alarm, they will use the diagnostic tools provided by the network management software to analyze the fault and determine the cause of the fault (such as equipment hardware failure, software failure, network attack, etc.). For hardware failures, damaged equipment will be replaced in time; for software failures, the software program will be remotely updated or repaired; for network attacks, corresponding security protection measures will be taken, such as adjusting firewall policies, updating encryption keys, etc., to ensure the network can quickly return to normal operation. Regularly upgrade the software of the wireless ad hoc network equipment, fix known vulnerabilities, optimize performance, and add new functions. Before software upgrading, thorough testing is conducted to ensure that the upgrade process will not affect the normal operation of the network. At the same time, the network management software is maintained, important data is backed up, the database structure is optimized, and the stability and response speed of the system are improved.
VII. Safety Assurance Measures
Advanced encryption algorithms (such as AES - 256) are adopted to encrypt the transmitted data, preventing it from being stolen or tampered with during transmission. A secure key exchange mechanism is established between nodes, and the encryption keys are updated regularly to ensure the security of data transmission. Strict access control policies are set, allowing only authorized users and devices to access the network. Multiple authentication methods such as username and password authentication, digital certificate authentication, etc. are used to ensure the legitimacy of user identities. At the same time, different access permissions are assigned to different users and devices, restricting their access scope to network resources and preventing illegal operations. An intrusion detection system (IDS) and an intrusion prevention system (IPS) are deployed to monitor abnormal behaviors and attack signals in the network in real time. When a network attack is detected, the system automatically takes defensive measures, such as blocking the attack source and isolating infected nodes, to protect network security.